Introduction:
In today's digital era, ensuring the security of sensitive documents is paramount. QR codes have emerged as a versatile tool for document security, offering efficient and reliable methods to protect information. In this article, we will explore two popular security models implemented using QR codes: the Link-Model and the Crypto-Model. We will define and compare these models to help you determine which one best suits your specific security requirements.
1. Link-Model:
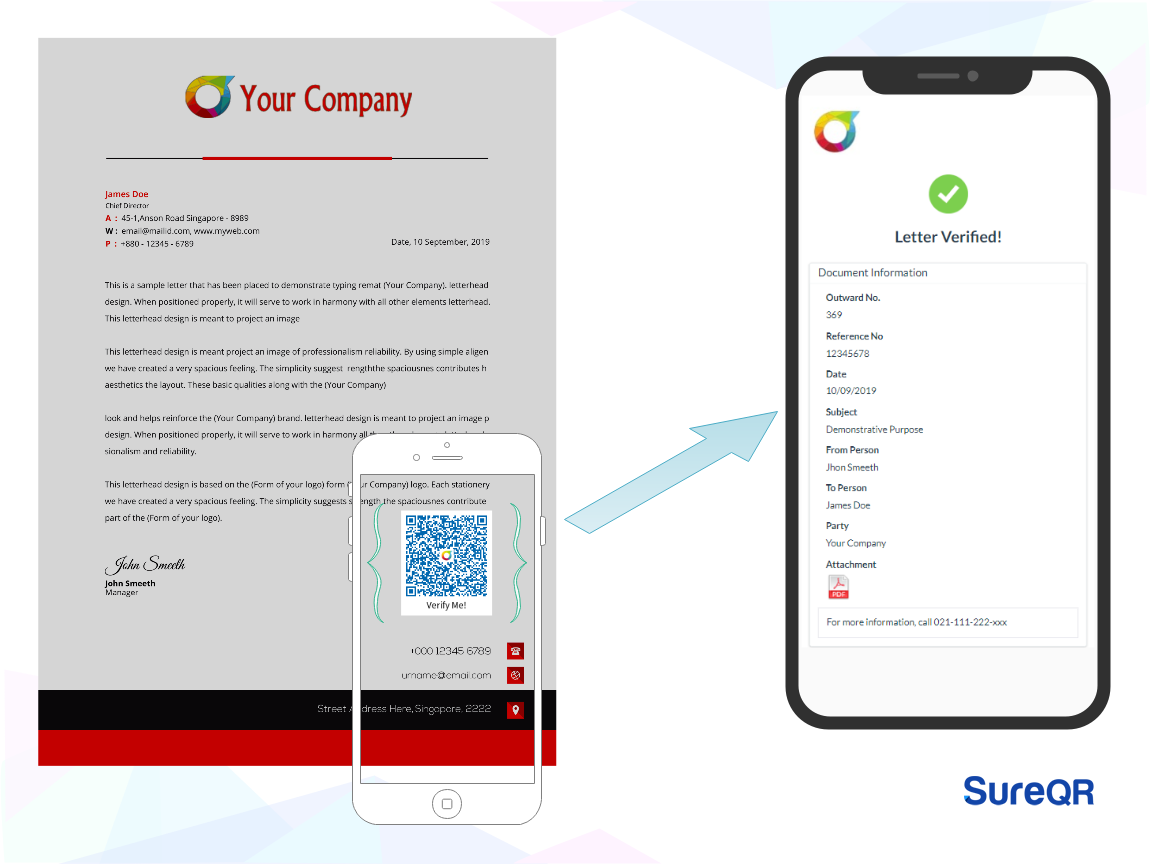
Document security using QR codes with embedded URLs is a technique used to verify the authenticity and integrity of official documents, particularly where short-term security or documents with a validity period or expiry date are required. This approach is also preferred for documents that are not expected to be useful for long terms, such as COVID-19 certificates, account statements from banks, payslips from companies, and lab reports. Here's how it works:
- Embedded URL: The QR code on the document contains a URL that links to the official website of the issuing body, such as a government agency or a healthcare organization.
- Official Domain: The URL embedded in the QR code must be on the official domain of the issuing body, ensuring that the information can be accessed from a trusted and verified source.
- Verification Process: When the QR code is scanned, the user's device is directed to the URL, which typically leads to a verification page. This page retrieves the document's information from the issuing body's database and displays the relevant details, such as the document type, issue date, and other relevant information.
- Authenticity Validation: The verification process allows the user to confirm that the document is authentic and has been issued by the official body, as the information displayed on the verification page is directly pulled from the issuing body's records.
It helps to prevent fraudulent activities and ensures that the information presented on the document can be trusted.
Advantages:
- Ease of use: The Link-Model is user-friendly, requiring only a QR code scanner app to access the document.
- Convenient updates: If the document is updated or modified, the URL remains the same, eliminating the need to generate a new QR code.
- Scalability: This model is suitable for scenarios where documents are frequently updated and shared among a large number of users.
Limitations:
- Dependency on internet connectivity: As the document is stored online, accessing it requires a stable internet connection.
- Potential vulnerabilities: If the hosting server is compromised, the document's security can be compromised as well.
- Database Manipulation: If an IT professional or administrator with access to the database adds a record, the system can be easily manipulated, potentially enabling the issuance of fake degrees or other fraudulent documents.
2. Crypto-Model:
This model secures documents using cryptography. It is the process of ensuring the authenticity, integrity, and non-repudiation of a document through incorporating the metadata of the document (also called the message) and digital signature inside the QR code, particularly where long-term security is required.. Unlike the URL-based method, this approach is preferred when the document is expected to be useful for an extended period.
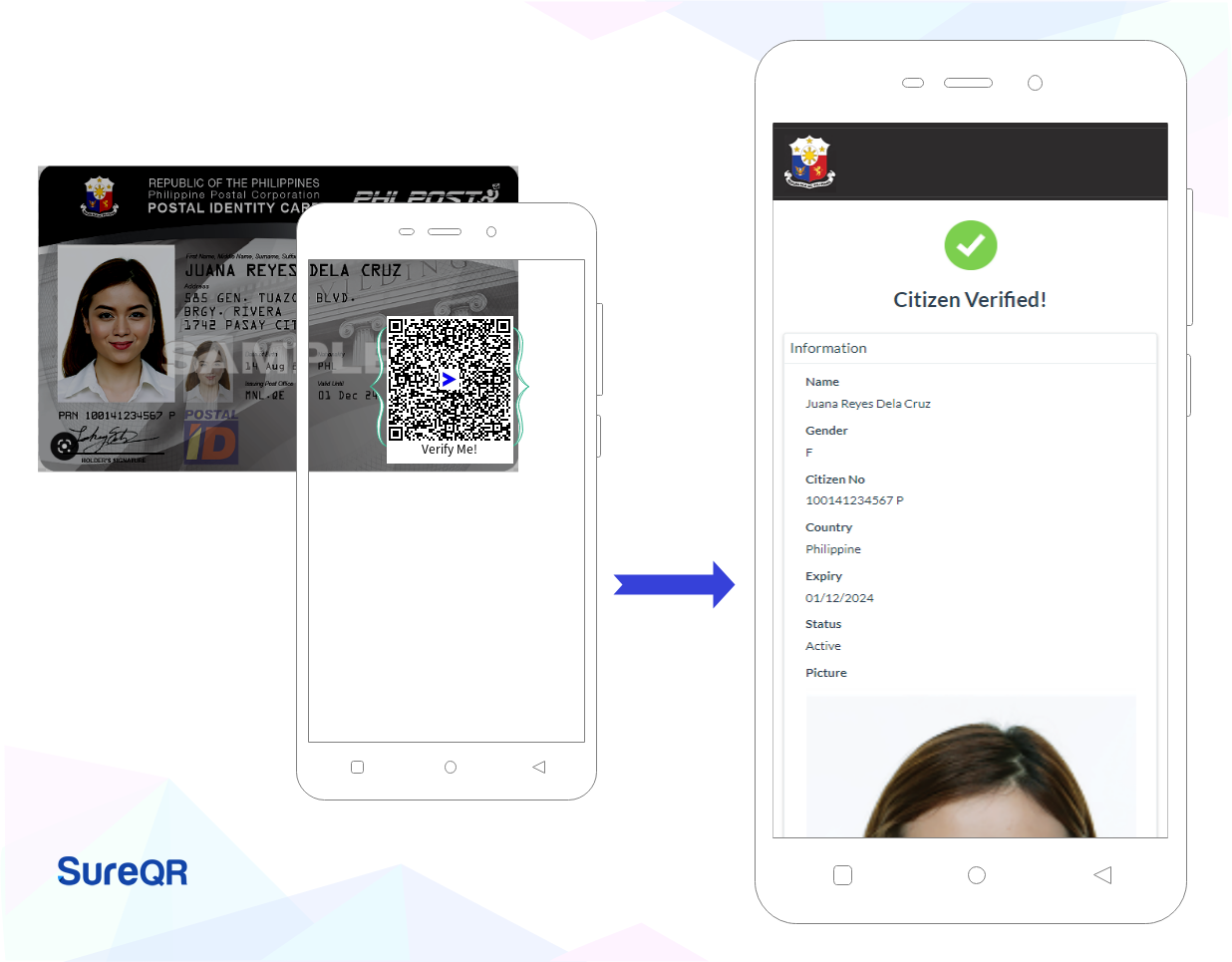
- QR Code: The QR code on the document contains the document's key information, such as the document type, issue date, and other relevant details. This is called the message. Additionally, the QR code also contains a digital signature of the message.
- Digital Signature: The document information stored in the QR code is digitally signed using the issuing body's private key, ensuring the integrity and authenticity of the data.
- Offline Verification: To enable offline verification, the issuing body's public key (security key) is also included in the QR code or printed alongside it. This allows the document's recipient to verify the digital signature without the need for an active internet connection.
- Verification Process: When the QR code is scanned, the document information (the message) and the digital signature are extracted. The recipient can then use the public key to verify the signature, confirming the document's authenticity and ensuring that the information has not been tampered with. Additionally, for user's convenience and increased trust, a validation page is published on the website of the document issuer that allows users to upload a digital copy of the document and conveniently see the result of the verification.
- Long-Term Security: This approach provides long-term security for the document, as the digital signature and the included public key ensure the document's integrity and authenticity even after the issuing body's website or verification service is no longer available.
This system of document security using QR codes with embedded messages and digital signatures is particularly useful for documents that are expected to have long-term usefulness, such as academic certificates, professional licenses, property documents, or important legal documents. It ensures that the document can be verified offline, and the authenticity and integrity of the information can be trusted even in the absence of the issuing body's online verification service.
Advantages:
- Offline Verification: The inclusion of the issuing authority's public key allows the document's authenticity to be verified offline, without the need for an active internet connection or access to the issuing body's website.
- Long-Term Reliability: The digital signature and embedded public key ensure the document's integrity and authenticity can be verified even if the issuing body's website or verification service is no longer available in the future.
- Tamper-Evidence: The digital signature makes it possible to detect if the document's content has been tampered with or altered since it was issued.
Limitations:
- Complexity: Implementing the encryption model requires additional technical expertise to sign and verify documents securely.
- Dependency on Issuing Authority: The security of this approach is heavily dependent on the issuing authority maintaining the integrity of its private key and the overall security of its systems. However, SureQR overcomes this limitation by integrating a Key Management System (KMS) server as an essential component.
- Maintenance: If the document is updated, a new QR code needs to be generated and distributed to authorized individuals.
Conclusion:
Both models offer robust security features that can help establish trust and integrity for critical documents. However, each approach has its own strengths and weaknesses that should be carefully evaluated based on the specific requirements and use cases.
The Link-Model provides a strong foundation by embedding verified links to the issuing authority's website, allowing users to directly confirm the document's authenticity. This approach is relatively straightforward and can be easily integrated into existing document workflows. However, it relies on the continued availability and accessibility of the issuing authority's website, which could be a limitation in certain scenarios.
In contrast, the Crypto-Model with QR codes, digital signatures, and embedded messages offers a more comprehensive security solution. By leveraging cryptographic techniques, this approach can provide offline verification, tamper-evidence, and long-term reliability - even if the issuing authority's website or verification service is no longer accessible in the future. The integration of a dedicated Key Management System (KMS) server further enhances the security by isolating the management of the issuing authority's private keys, reducing the attack surface and improving overall resilience.
Ultimately, the choice between these two security models will depend on the specific requirements of the document use case, the desired level of security, the technical capabilities of the issuing authority and the end-users, and the overall cost-benefit analysis. For scenarios where long-term document integrity, offline verification, and resilience against potential website or service disruptions are critical, the Crypto-Model with the KMS server integration may be the more suitable solution. Conversely, the link model may be a more practical choice for applications where the emphasis is on simplicity, ease of implementation, and direct website verification.
By understanding the strengths and limitations of each approach, organizations can make an informed decision and implement the document security solution that best aligns with their security requirements, technological constraints, and user expectations.
Register with SureQR and start generating and printing QR codes on your degrees and certificates in 5 minutes